Reasons to prefer blake3 over sha256
Published: Tue 09 May 2023
This post is a copy of tweets by Zooko Wilcox-O'Hearn.
SHA256 was designed by the NSA. BLAKE (the original) and BLAKE3 were designed by Jean-Philippe Aumasson and others (including me, but Jean-Philippe and the other contributors did a lot more of the cryptographic heavy lifting than I did).
SHA256 was based on SHA1 (which is weak). BLAKE was based on ChaCha20, which was based on Salsa20 (which are both strong).
NIST/NSA have repeatedly signaled lack of confidence in SHA256: first by hastily organising the SHA3 contest in the aftermath of Wang's break of SHA1, then by making "Don't be like SHA256" a goal for the algorithms of that contest, and then by banning SHA256 from new designs to be used by the USA government (except for in one specific cryptosystem that protects from weaknesses in the hash function https://media.defense.gov/2022/Sep/07/2003071836/-1/-1/0/CSI_CNSA_2.0_FAQ_.PDF).
BLAKE (the original) was very well-studied during the SHA3 competition. In NIST's final report on the SHA3 process, they stated that the depth of scientific analysis applied to BLAKE exceeded even that applied to Keccak (the final SHA3 winner).

Known, feasible attacks can break 31 out of 64 rounds of SHA256 (48% of the rounds). Known, feasible attacks can break only 2 out of 7 rounds of BLAKE3 (29% of the rounds).
BLAKE3 comes “out of the box” with security features that can protect users in common use cases, such as protection against length-extension attack, a standard method of keying, "personalization tags" to guarantee domain separation, etc.
BLAKE3 is much more efficient (in time and energy) than SHA256, like 14 times as efficient in typical use cases on typical platforms.
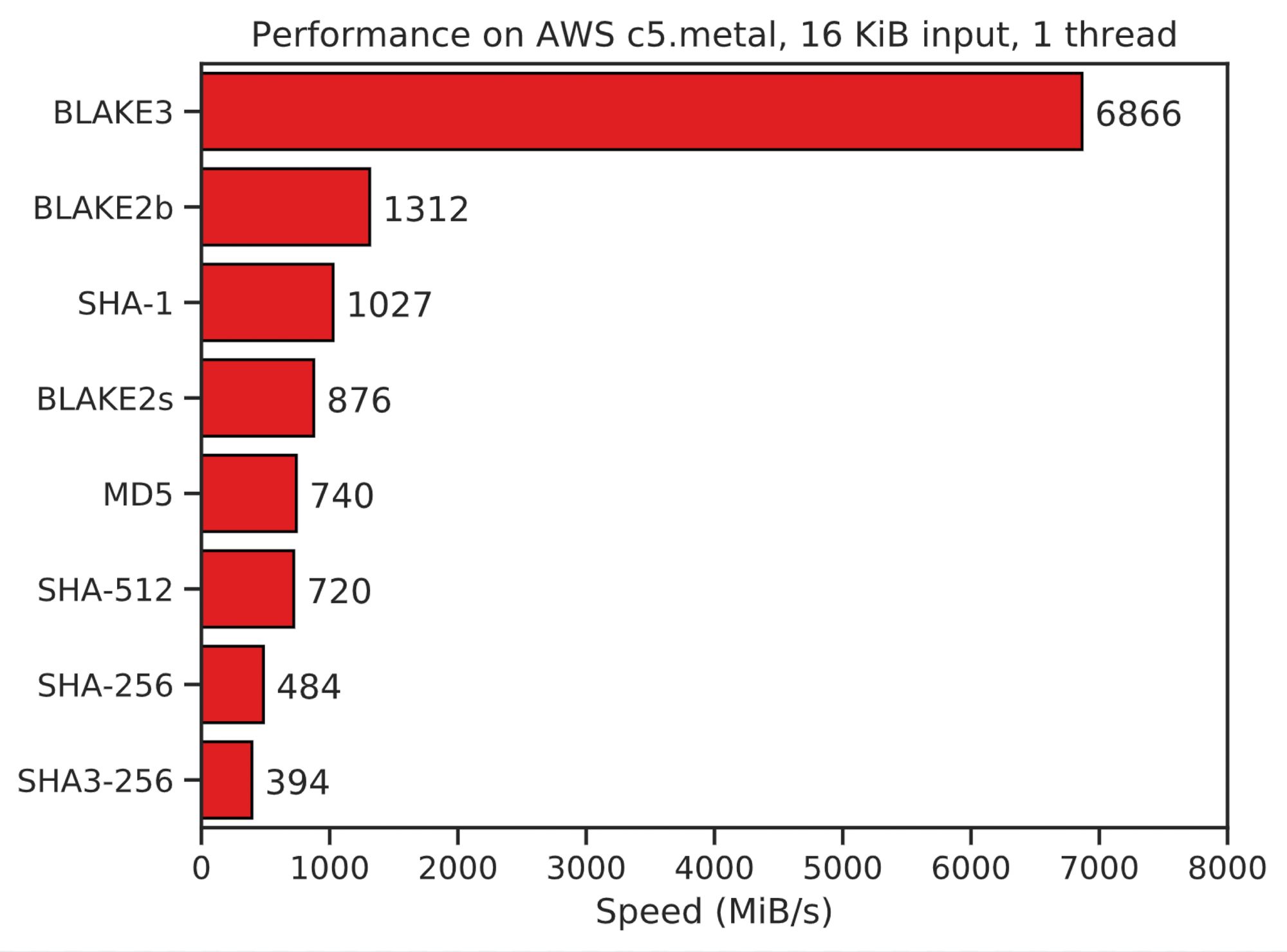
BLAKE3 also offers performance that is competitive against SHA256 in a lot of different use cases and platforms, including some that might surprise you, such as sometimes being more efficient than SHA256 even when your CPU comes with SHA256 acceleration circuits built into it!
BLAKE3 is highly parallelizable. This provides two performance advantages, only the first of which most people think about.
-
The first is big data + big multicore: if the size of your data inputs scale up 100X but the number of CPU cores in your platform also scale up 100X, BLAKE3 takes only a little longer, but SHA256 takes approximately 100X times as long.
-
The other advantage, less widely understood, is that inside a single compute device, new tech improvements provide more and more parallel power. This is true in FPGAs and GPUs, and it is true in CPUs because of vectorization upgrades.
AVX in Intel/AMD, Neon and Scalable Vector Extensions in Arm, and RISC-V Vector computing in RISC-V. BLAKE3 can take advantage of all of it.
When you upgrade to a newer CPU/platform/device, BLAKE3 typically further extends its performance advantage over SHA256 compared to the performance advantage it already had on the previous platform!
Finally, BLAKE3 was designed and implemented by both cryptographers and software engineers. The reference implementations are super efficient and well-engineered for security, thanks to Jack O'Connor, Samuel Neves, and Jean-Philippe Aumasson: https://github.com/BLAKE3-team/BLAKE3
End of quote. You can follow our progress on upgrading to blake3 here.
RECENT POSTS
- 2025 - What a year!
- Decentralization Matters
- Security audit 2024
- Reasons to prefer blake3 over sha256
- A better web
- Markdown browser
- Release the BATs (block level access control in IPFS)
- Encrypted email storage and client
- Decentralized encrypted chat
- Peergos launches decentralized & encrypted social media
- Private and customizable profiles
- Simple decentralized web hosting on Peergos
- Encrypted shareable calendar
- Fast Encrypted File Search
- Private Planning Boards in Peergos
- How to solve the social dilemma and fix social media
- Peergos wins EU Next Generation Internet grant
- Direct S3 access
- Peergos release v0.3.0
- Keybase has left the building
- The perfect social network
- Atomic access control
- Peergos release v0.1.3
- Applications on Peergos
- Fast seeking and encrypted history
- IPFS Camp, new features
- Alpha Release
- Security Audit
- Development update